Working with the Department of Defense isn’t just about delivering services; it’s about trust, especially when protecting vital information online. As cyber risks intensify, the DoD requires all partners to meet specific security standards such as the Cybersecurity Maturity Model Certification (CMMC). The crucial first step, CMMC Level 1 focuses on fundamental practices you might already be doing. However, knowing exactly which steps are required is the difference between securing a contract and missing out. Are you curious how straightforward (and essential) meeting Level 1 is? Your easy-to-follow guide and checklist are waiting below.
What is CMMC Compliance?
CMMC stands for Cybersecurity Maturity Model Certification. It’s a set of online security rules by the U.S. Department of Defense (DoD). The main goal is to ensure that companies working with the DoD, especially those aiming for CMMC level 1, have good security to protect their Federal Contract Information (FCI). Getting CMC compliance at level 1 shows you have the basic but essential online safety steps. This is often the first thing the DoD looks for in contracts.
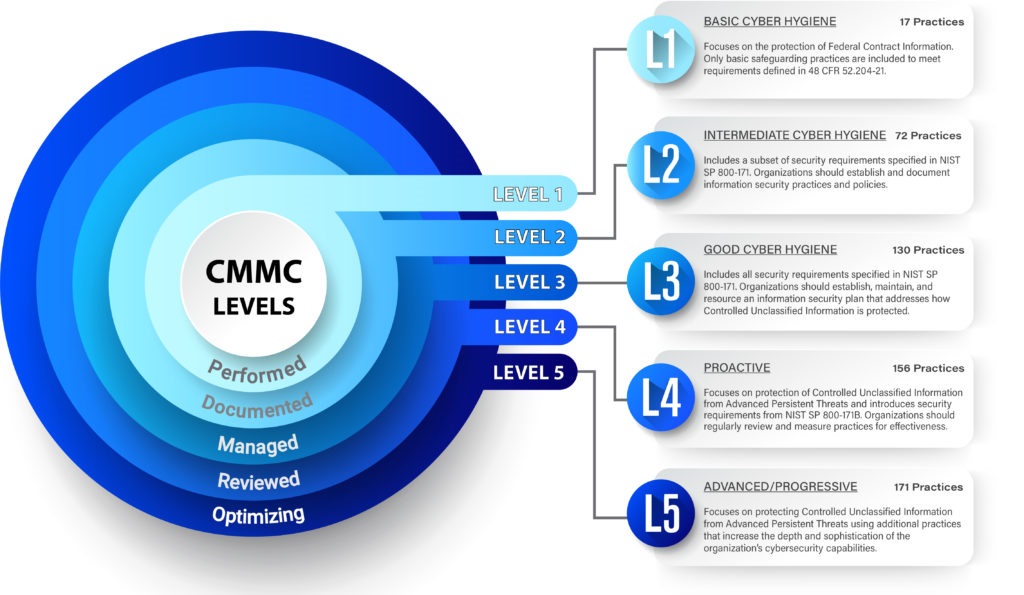
What Are the Different Levels of CMMC? Why Have Them?
The CMMC framework has different levels to match how secure different kinds of information are needed. Here’s a quick look:
- Level 1—Foundational: This starting point focuses on basic online safety to protect FCI. Our checklist includes the CMMI level 1 requirements.
- Level 2—Advanced: This level requires more advanced safety steps to protect Controlled Unclassified Information (CUI).
- Level 3 – Expert: This is the highest level, focused on protecting sensitive CUI from skilled attackers.
These levels exist so that the security matches the importance of the information. This helps all companies, big and small, meet the proper safety rules without being too complicated. For many companies new to DoD contracts, reaching CMMI level 1 is the first and most important step.
Checklist For CMMC Level 1
This checklist helps you determine whether your company is ready for CMMC Level 1 and provides a clear and easy way to check the official rules from FAR clause 52.204-21.
Access Control
Rule: [FAR 52.204-21(b)(1)(i)] Limit who can get into your computer systems.
Your FCI is private. Only trusted people and systems should touch it. Your data could be stolen or messed up if anyone can get in. This rule ensures that only the right people can reach the systems where you keep FCI.
- Action: Make sure only people, programs, or devices you approve can use systems with FCI. This is how you put the rule into action. By only letting approved users or devices connect, you build the first wall to stop bad people or bad software from getting to your FCI. It’s the main way to control who can access your sensitive data.
- Evidence: Have lists of approved users, notes on who manages accounts, and papers showing who is allowed access. These papers show you have a system for deciding and tracking who is approved. It proves you are doing this step.
Rule: [FAR 52.204-21(b)(1)(ii)] Limit what users can do on the systems.
Even people you trust don’t need to do everything on your systems. Giving users too many powers makes it easier for them to accidentally or purposely harm FCI. This rule is about giving people only the power they truly need.
- Action: Give people only the computer access they need to do their job. This step follows the “need to know” idea. Limiting what each user can do (like stopping them from installing programs or only letting them see certain FCI files) lowers the chance they will damage systems or data.
- Evidence: Record how you set up access based on people’s jobs. Have papers showing what each person is allowed to do. This shows you set up access carefully based on what people need for work.
Rule: [FAR 52.204-21(b)(1)(iii)] Check and limit connections to outside computer systems
Connecting to other networks (like the internet) is like having doors to your system. Bad things can come in, and your FCI could leak out. This rule says you must control these doors.
- Action: Create rules for how your systems connect to other systems and monitor these connections. This will set up safety walls around your network. Using tools like firewalls can help you decide what kind of online traffic is allowed in or out. You can block bad traffic and spot strange activity. This will prevent outsiders from accessing your FCI systems and prevent FCI from being sent out when it shouldn’t be.
- Evidence: Show the rules for your firewall. Explain how your VPN works. Have written rules about connecting to systems outside your network. These show the technical and written rules you use at your network’s edge.
Rule: [FAR 52.204-21(b)(1)(iv)] Control what information goes online.
Putting FCI on public websites or online services by mistake is a big problem. It would mean the data is no longer private. This rule makes sure you check things before they go public.
- Action: Check information carefully before you put it online to ensure no FCI is visible. This step adds a check before you share anything publicly. By looking at content before it goes online, you add an extra layer of safety. This helps ensure your FCI stays private inside your network.
- Evidence: Explain how you check website content. Show your written steps for handling data on public systems. This shows the process you follow to keep FCI off public sites.
Identification and Authentication
Rule: [FAR 52.204-21(b)(2)(i)] Know who or what is using your computer systems.
You can’t protect systems with FCI if you don’t know who is using them. Giving everyone a unique name is the first step to tracking what happens and who is responsible.
- Action: Give every person and every device a unique ID or name. This ensures that you can tell each user and device apart when they use your systems. Knowing who did what (like looking at or changing FCI) is key for monitoring problems and determining who is allowed to do what. Without unique IDs, everyone looks the same.
- Evidence: Have lists of user accounts and records of all your devices. These lists are like a roster of everyone and everything on your system.
Rule: [FAR 52.204-21(b)(2)(ii)] Make sure users are who they say they are before they get access.
Just having a name isn’t enough. You need to be sure the person using that name is the real person. Easy ways to log in let attackers pretend to be real users and get to your FCI.
- Action: Use strong passwords and multi-factor authentication (MFA). This makes checking identities much stronger. Strong passwords are hard to guess. MFA asks for more than one proof of identity (like a password plus a code from your phone). Using both makes it much harder for someone who shouldn’t be there to log in, even if they find a password. This protects the door to your FCI systems.
- Evidence: Show your rules for making passwords. Explain how MFA is set up. Show records of who logs in. These show the rules and tools you use to check who people are.
Media Protection
Rule: [FAR 52.204-21(b)(3)(i)] Safely erase or destroy old storage with Federal Contract Information.
When you are done with hard drives, USB sticks, or papers that had FCI, just deleting files or throwing them away isn’t safe enough. The FCI can often still be found later. This rule ensures FCI is truly gone when you no longer need it.
- Action: Have clear steps for safely erasing or breaking old hard drives, USB drives, and paper documents that hold FCI. This puts safe ways for getting rid of data into practice. Properly erase data and write over it many times so no one can read it. Breaking the media makes the data impossible to get. These steps are needed to stop your old FCI from getting in the wrong hands.
- Evidence: Show your rules for destroying data. Include records of when you erased or shredded things. These rules show how you safely get rid of data.
Physical Protection
Rule: [FAR 52.204-21(b)(4)(i)] Limit who can physically get to your computer equipment.
If someone can touch your computers or servers, they can get around your network security. They could steal equipment or grab data directly. This rule protects the actual place where your computer equipment sits.
- Action: Control who can enter rooms where you keep servers and other computer gear. This creates physical barriers and watching eyes to stop unapproved people from touching your key computer gear. Limiting entry to secure rooms stops people from changing things, stealing gear, or directly reaching the computers with FCI. This adds a key safety layer beyond just network protection.
- Evidence: Keep records of who goes in and out. Have security camera videos. Use visitor sign-in sheets. These show you control and watch who is physically in the area.
System and Communications Protection
Rule: [FAR 52.204-21(b)(5)(i)] Watch and protect how information moves in and out of your network.
Data, like your FCI, travels through your network. If you don’t watch and control this traffic, bad things can come in, and sensitive data can leak without anyone knowing. This rule focuses on keeping the flow of information safe.
- Action: Use firewalls and other security tools to monitor and control what moves on your network. Technical tools filter and monitor your network traffic. Firewalls block bad connections based on your rules. Watching tools spot strange patterns that might indicate an attack or someone trying to steal data. This is needed to stop outside threats from getting to your FCI systems.
- Evidence: Show how your firewall is set up. Provide maps of your network. Show records from tools that find threats. This proves you have rules and that you should watch your network edges.
Rule: [FAR 52.204-21(b)(5)(ii)] Keep public-facing computer systems separate from your main network.
Systems anyone on the internet can reach (like your website) are more likely to be attacked. If these are directly connected to your internal network where you keep FCI, a hack on the public system could lead straight to your private data.
- Action: If you have public websites or systems, ensure they are in a different part of your network than the one with FCI. Use separate areas (like a DMZ). This creates a safe space between your public systems and your inner network with FCI. If a public system is hacked, the attacker is stuck in this separate area and can’t easily get to your internal FCI network, helping limit the damage.
- Evidence: Show maps of your network and explain how it’s set up with different sections. This shows how you separate public systems from sensitive data.
System and Information Integrity
Rule: [FAR 52.204-21(b)(6)(i)] Find and fix computer problems quickly.
Computer programs often have weaknesses that attackers can use to break in or cause trouble and get to FCI. Not fixing these weaknesses is a big security risk.
- Action: Have a way to find, report, and fix security problems in your systems and software. This will allow you to fix problems before they are used against you. Finding weaknesses often (like scanning) and quickly adding updates closes doors that attackers could use to harm systems and get or mess up FCI. This gives attackers less time to use their weaknesses.
- Evidence: Show reports from checking for weaknesses. Show records of when you added updates. Show reports about security problems found. This proves you have a plan for finding and fixing issues.
Rule: [FAR 52.204-21(b)(6)(ii)] Protect your systems from bad software like viruses.
Bad software (like viruses or ransomware) can stop your systems from working, steal your data (like FCI), or give attackers control. Stopping this bad software is key to keeping your systems and FCI safe.
- Action: Use anti-malware software on all your computers. Keep it current. This adds a main tool to fight common threats. Anti-malware software finds and removes bad programs that could harm systems with FCI. Putting it on all needed computers means you have protection everywhere.
- Evidence: Show records of where the anti-malware software is installed, scan logs, and an explanation of how it’s set up. This confirms that the software is on your systems and working.
Rule: [FAR 52.204-21(b)(6)(iii)] Make sure your antivirus software is always up to date.
New bad software appears all the time. Anti-malware software needs updates to know what the latest threats look like. Old software won’t spot new viruses, leaving your systems and FCI open to attack.
- Action: Make sure your anti-malware software gets the latest updates often. This ensures your anti-malware defense is strong. Regularly updating the software and its threat lists helps it find and stop the newest types of bad software. This keeps your defense ready against changing dangers that could target your FCI.
- Evidence: Show records of when the anti-malware software was updated. Explain how it’s set to get updates. This proves the software is kept current to fight new threats.
Awareness and Training
Rule: [FAR 52.204-21(b)(7)(i)] Teach everyone who uses your systems about basic security
Attackers often trick people (for example, with fake emails) or make mistakes that cause security issues. People need to know the dangers of FCI and how to protect against it. Security is a job for everyone.
- Action: Provide regular security training for all employees and anyone else using your systems. Teach them about passwords, fake emails (phishing), and handling data safely. This teaches users how to spot and avoid common threats. It helps them understand the rules for keeping FCI safe. Training helps your people become a human defense wall. They learn to see fake emails, create good passwords, and know why protecting FCI is important. This greatly lowers the risk of problems caused by human mistakes or tricks.
- Evidence: Show what training materials you use, who attended, and when the training happened. This proves you are teaching your team.
Incident Response
Rule: [FAR 52.204-21(b)(8)(i)] Have a plan for what to do if there’s a security problem.
Even with good safety steps, security problems can still happen. If you don’t have a plan, a problem can cause more harm, last longer, and lead to wrong steps being taken. This could mean more data is lost or stolen.
- Action: Create and keep current a plan that says exactly what steps to take if a security issue happens. The plan must include telling the right people, as your contracts may require. This prepares you to act fast and well when a security issue hits. A clear plan means less confusion. It tells you how to stop the problem and fix the affected systems and data (like FCI). It includes steps for telling others (like the government if your contract says so). This helps limit the damage and get things back to normal faster.
- Evidence: Show the paper document with your incident response plan, forms for reporting problems, and records of any problems that occurred. These show that you have a plan and follow it.
Getting to CMMC Level 1 is a good first step. It helps you work with the DoD. It also shows you care about computer safety. Just use this easy list. Learn the main CMMC Level 1 rules. This helps your company start the right way. At Defend My Business, we know these first steps matter. We can help you understand the CMMC rules. Keep working on being secure. You will be on your way to success.
- What is FCI?
FCI (Federal Contract Information) is basic government information used in contracts that isn’t for the public. You need to protect it at cmmc level 1.
- Do I need someone else to check my CMMC Level 1 compliance?
For CMMC Level 1, you usually do a self-assessment. You check your own company against the CMMC Level 1 requirements.
- How long will it take to meet CMMC Level 1 rules?
It depends on how secure you are now. If you already have some good security, it might be faster. If you’re starting new, meeting all the cmmc level 1 requirements could take longer.
- Where can I learn more about CMMC Level 1?
The best place is the Department of Defense website on CMMC: https://dodcio.defense.gov/cmmc/. There, you can find information on level 1 requirements.
- What if I don’t meet CMMC Level 1?
If you don’t meet the required cmmc level, you might not be able to get DoD contracts that need it.